Question 1
A security analyst discovers the following firewall log entries during an incident:

Which of the following is MOST likely occurring?
A. Banner grabbing
B. Port scanning
C. Beaconing
D. Data exfiltration
Correct Answer: B
Question 2
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations.
To help mitigate this risk, the Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
A. Data masking procedures
B. Enhanced encryption functions
C. Regular business impact analysis functions
D. Geographic access requirements
Correct Answer: D
Question # 3
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:

Which of the following ports should be closed?
A. 21
B. 80
C. 443
D. 1433
Correct Answer: D
Question 4
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:

Follow TCP stream:
Which of the following describes what has occurred?
A. The host attempted to download an application from utoftor.com.
B. The host downloaded an application from utoftor.com.
C. The host attempted to make a secure connection to utoftor.com.
D. The host rejected the connection from utoftor.com.
Correct Answer: B
Question 5
Which of the following organizational initiatives would be MOST impacted by data sovereignty issues?
A. Moving to a cloud-based environment
B. Migrating to locally hosted virtual servers
C. Implementing non-repudiation controls
D. Encrypting local database queries
Correct Answer: A
Question 6
HOTSPOT –
A security analyst suspects that a workstation may be beaconing to a command and control server.
Inspect the logs from the company’s web proxy server and the firewall to determine the best course of action to take in order to neutralize the
threat with minimum impact to the organization.
INSTRUCTIONS –
Modify the Firewall Access Control rule to mitigate the issue.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.




Correct Answer:

Question 7
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company’s single Internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT department?
A. Require the guest machines to install the corporate-owned EDR solution
B. Configure NAC to only allow machines on the network that are patched and have active antivirus
C. Place a firewall in between the corporate network and the guest network
D. Configure the IPS with rules that will detect common malware signatures traveling from the guest network
Correct Answer: B
Question 8
Which of the following describes the main difference between supervised and unsupervised machine-learning algorithms that are used in cybersecurity applications?
A. Supervised algorithms can be used to block attacks, while unsupervised algorithms cannot.
B. Supervised algorithms require security analyst feedback, while unsupervised algorithms do not.
C. Unsupervised algorithms are not suitable for IDS systems, while supervised algorithms are.
D. Unsupervised algorithms produce more false positives than supervised algorithms.
Correct Answer: B
Question 9
Which of the following is MOST closely related to the concept of privacy?
A. The implementation of confidentiality, integrity, and availability
B. A system’s ability to protect the confidentiality of sensitive information
C. An individual’s control over personal information
D. A policy implementing strong identity management processes
Correct Answer: C
Question # 10
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content. Which of the following is the NEXT step the analyst should take?
A. Validate the binaries’ hashes from a trusted source.
B. Use file integrity monitoring to validate the digital signature.
C. Run an antivirus against the binaries to check for malware.
D. Only allow whitelisted binaries to execute.
Correct Answer: A
Question 11
As part of an intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several domains and reputational information that suggest the company’s employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for intelligence gathering?
A. Update the whitelist.
B. Develop a malware signature.
C. Sinkhole the domains.
D. Update the blacklist.
Correct Answer: C
Question 12
A small organization has proprietary software that is used internally. The system has not been well maintained and cannot be updated with the rest of the environment. Which of the following is the BEST solution?
A. Virtualize the system and decommission the physical machine.
B. Remove it from the network and require air gapping.
C. Implement privileged access management for identity access.
D. Implement MFA on the specific system.
Correct Answer: B
Question 13
A security analyst reviews SIEM logs and discovers the following error event:

Which of the following environments does the analyst need to examine to continue troubleshooting the event?
A. Proxy server
B. SQL server
C. Windows domain controller
D. WAF appliance
E. DNS server
Correct Answer: E
Question 14
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:

Which of the following technologies would MOST likely be used to prevent this phishing attempt?
A. DNSSEC
B. DMARC
C. STP
D. S/IMAP
Correct Answer: B
Question 15
A security analyst is reviewing a vulnerability scan report and notes the following finding:

As part of the detection and analysis procedures, which of the following should the analyst do NEXT?
A. Patch or reimage the device to complete the recovery.
B. Restart the antiviruses running processes.
C. Isolate the host from the network to prevent exposure.
D. Confirm the workstation’s signatures against the most current signatures.
Correct Answer: D
Question 16
A security analyst identified one server that was compromised and used as a data mining machine, and a clone of the hard drive that was created.
Which of the following will MOST likely provide information about when and how the machine was compromised and where the malware is located?
A. System timeline reconstruction
B. System registry extraction
C. Data carving
D. Volatile memory analysis
Correct Answer: A
Question 17
A company frequently experiences issues with credential stuffing attacks. Which of the following is the BEST control to help prevent these attacks from being successful?
A. SIEM
B. IDS
C. MFA
D. TLS
Correct Answer: C
Question 18
After an incident involving a phishing email, a security analyst reviews the following email access log:

Based on this information, which of the following accounts was MOST likely compromised?
A. CARLB
B. CINDYP
C. GILLIANO
D. ANDREAD
E. LAURAB
Correct Answer: D
Question 19
The incident response team is working with a third-party forensic specialist to investigate the root cause of a recent intrusion. An analyst was asked to submit sensitive network design details for review. The forensic specialist recommended electronic delivery for efficiency, but email was not an approved communication channel to send network details. Which of the following BEST explains the importance of using a secure method of communication during incident response?
A. To prevent adversaries from intercepting response and recovery details
B. To ensure intellectual property remains on company servers
C. To have a backup plan in case email access is disabled
D. To ensure the management team has access to all the details that are being exchanged
Correct Answer: A
Question 20
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server. Suspecting the system may be compromised, the analyst runs the following commands:

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
A. Run crontab -r; rm -rf /tmp/.t to remove and disable the malware on the system.
B. Examine the server logs for further indicators of compromise of a web application.
C. Run kill -9 1325 to bring the load average down so the server is usable again.
D. Perform a binary analysis on the /tmp/.t/t file, as it is likely to be a rogue SSHD server.
Correct Answer: B
Question 21
Which of the following are considered PI I by themselves? (Choose two.)
A. Government ID
B. Job title
C. Employment start date
D. Birth certificate
E. Employer address
F. Mother’s maiden name
Correct Answer: AD
Question 22
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL:

Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
A. PC1
B. PC2
C. Server1
D. Server2
E. Firewall
Correct Answer: E
Question 23
The security team decides to meet informally to discuss and test their response plan for potential security breaches and emergency situations.
Which of the following types of training will the security team perform?
A. Tabletop exercise
B. Red-team attack
C. System assessment implementation
D. Blue-team training
E. White-team engagement
Correct Answer: A
Question 24
A security analyst is investigating an incident related to an alert from the threat detection platform on a host (10.0.1.25) in a staging environment that could be running a cryptomining tool because it is sending traffic to an IP address that is related to Bitcoin.
The network rules for the instance are the following:

Which of the following is the BEST way to isolate and triage the host?
A. Remove rules 1, 2, and 3.
B. Remove rules 1, 2, 4, and 5.
C. Remove rules 1, 2, 3, 4, and 5.
D. Remove rules 1. 2, and 5.
E. Remove rules 1, 4, and 5.
F. Remove rules 4 and 5.
Correct Answer: D
Question 25
While conducting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:

Based on the Prowler report, which of the following is the BEST recommendation?
A. Delete CloudDev access key 1.
B. Delete BusinessUsr access key 1.
C. Delete access key 1.
D. Delete access key 2.
Correct Answer: B
Question 26
When investigating a report of a system compromise, a security analyst views the following /var/log/secure log file:

Which of the following can the analyst conclude from viewing the log file?
A. The comptia user knows the sudo password.
B. The comptia user executed the sudo su command.
C. The comptia user knows the root password.
D. The comptia user added himself or herself to the /etc/sudoers file.
Correct Answer: C
Question 27
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team’s NEXT step during the detection phase of this response process?
A. Escalate the incident to management, who will then engage the network infrastructure team tokeep them informed.
B. Depending on system criticality, remove each affected device from the network by disabling wired and wireless connections.
C. Engage the engineering team to block SMB traffic internally and outbound HTTP traffic to the five IP addresses.
D. Identify potentially affected systems by creating a correlation search in the SIEM based on the network traffic.
Correct Answer: D
Question 28
Which of the following types of controls defines placing an ACL on a file folder?
A. Technical control
B. Confidentiality control
C. Managerial control
D. Operational control
Correct Answer: A
Question 29
A security analyst is reviewing the following Internet usage trend report:

Which of the following usernames should the security analyst investigate further?
A. User 1
B. User 2
C. User 3
D. User 4
Correct Answer: B
Question 30
During a review of the vulnerability scan results on a server, an information security analyst notices the following:

The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
A. it only accepts TLSv1 .2.
B. it only accepts cipher suites using AES and SHA.
C. it no longer accepts the vulnerable cipher suites.
D. SSL/TLS is offloaded to a WAF and load balancer.
Correct Answer: C
Question 31
A Chief Information Security Officer (CISO) is concerned developers have too much visibility into customer data. Which of the following controls should be implemented to BEST address these concerns?
A. Data masking
B. Data loss prevention
C. Data minimization
D. Data sovereignty
Correct Answer: A
Question 32
A company’s security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported, and patches are no longer available. The company is not prepared to cease its use of these workstations.
Which of the following would be the
BEST method to protect these workstations from threats?
A. Deploy whitelisting to the identified workstations to limit the attack surface.
B. Determine the system process criticality and document it.
C. Isolate the workstations and air gap them when it is feasible.
D. Increase security monitoring on the workstations.
Correct Answer: C
Question 33
Which of the following BEST describes how logging and monitoring work when entering into a public cloud relationship with a service provider?
A. Logging and monitoring are not needed in a public cloud environment.
B. Logging and monitoring are done by the data owners.
C. Logging and monitoring duties are specified in the SLA and contract.
D. Logging and monitoring are done by the service provider.
Correct Answer: C
Question 34
During routine monitoring, a security analyst identified the following enterprise network traffic:
Packet capture output:

Which of the following BEST describes what the security analyst observed?
A. 66.187.224.210 set up a DNS hijack with 192.168.12.21.
B. 192.168.12.21 made a TCP connection to 66.187.224.210.
C. 192.168.12.21 made a TCP connection to 209.132.177.50.
D. 209.132.177.50 set up a TCP reset attack to 192.168.12.21.
Correct Answer: C
Question 35
An organization needs to limit its exposure to accidental disclosure when employees send emails that contain personal information to recipients outside the company. Which of the following technical controls would BEST accomplish this goal?
A. DLP
B. Encryption
C. Data masking
D. SPF
Correct Answer: A
Question 36
A software developer is correcting the error-handling capabilities of an application following the initial coding of the fix. Which of the following would the software developer MOST likely perform to validate the code prior to pushing it to production?
A. Web-application vulnerability scan
B. Static analysis
C. Packet inspection
D. Penetration test
Correct Answer: B
Question 37
A security analyst has received a report that servers are no longer able to connect to the network. After many hours of troubleshooting, the analyst determines a Group Policy Object is responsible for the network connectivity issues. Which of the following solutions should the security analyst recommend to prevent an interruption of service in the future?
A. CI/CD pipeline
B. Impact analysis and reporting
C. Appropriate network segmentation
D. Change management process
Correct Answer: D
Question 38
HOTSPOT –
A security analyst performs various types of vulnerability scans.
Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
INSTRUCTIONS –
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for False Positives and check the Findings that display false positives.
NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server, and
Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:

Correct Answer:

Question 39
Which of the following are considered PII by themselves? (Choose two.)
A. Government ID
B. Job title
C. Employment start date
D. Birth certificate
E. Employer address
F. Mother’s maiden name
Correct Answer: AD
Question 40
A security analyst receives an alert to expect increased and highly advanced cyberattacks originating from a foreign country that recently had sanctions implemented. Which of the following describes the type of threat actors that should concern the security analyst?
A. Insider threat
B. Nation-threat
C. Hacktivist
D. Organized crime
Correct Answer: B
Question 41
A proposed network architecture requires systems to be separated from each other logically based on defined risk levels. Which of the following explains the reason why an architect would set up the network this way?
A. To complicate the network and frustrate a potential malicious attacker
B. To create a design that simplifies the supporting network
C. To reduce the attack surface of those systems by segmenting the network based on risk
D. To reduce the number of IP addresses that are used on the network
Correct Answer: C
Question 42
When investigating a compromised system, a security analyst finds the following script in the /tmp directory:

Which of the following attacks is this script attempting, and how can it be mitigated?
A. This is a password-hijacking attack, and it can be mitigated by using strong encryption protocols.
B. This is a password-spraying attack, and it can be mitigated by using multifactor authentication
C. This is a password-dictionary attack, and it can be mitigated by forcing password changes every 30 day.
D. This is a credential-stuffing attack, and it can be mitigated by using multistep authentication.
Correct Answer: B
Question 43
A company uses self-signed certificates when sending emails to recipients within the company. Users are calling the help desk because they are getting warnings when attempting to open emails sent by internal users. A security analyst checks the certificates and sees the following

Which of the following should the security analyst conclude?
A. [email protected] is a malicious insider.
B. The valid dates are too far apart and are generating the alerts
C. certServer has been compromised
D. The root certificate was not installed in the trusted store.
Correct Answer: D
Question 44
An organization wants to move non-essential services into a cloud computing environment. Management has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work BEST to attain the desired outcome?
A. Duplicate all services in another instance and load balance between the instances,
B. Establish a hot site with active replication to another region within the same cloud provider.
C. Set up a warm disaster recovery site with the same cloud provider in a different region.
D. Configure the systems with a cold site at another cloud provider that can be used for failover.
Correct Answer: C
Question 45
A security analyst is reviewing the following requirements for new time clocks that will be installed in a shipping warehouse:
• The clocks must be configured so they do not respond to ARP broadcasts.
• The server must be configured with static ARP entries for each clock.
Which of the following types of attacks will this configuration mitigate?
A. Spoofing
B. Overflows
C. Rootkits
D. Sniffing
Correct Answer: A
Question 46
A security analyst is probing a company’s public-facing servers for vulnerabilities and obtains the following output:
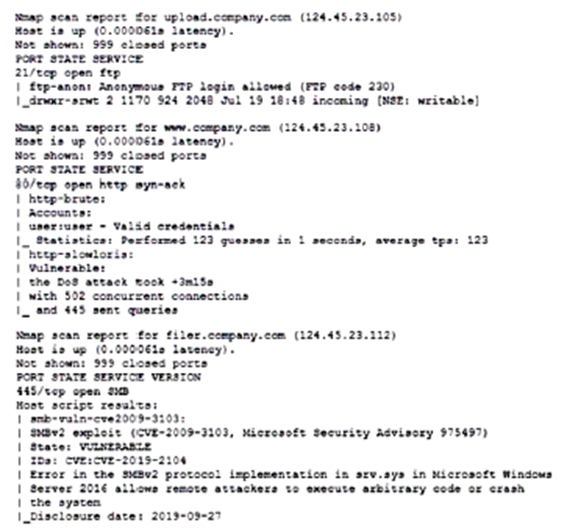
Which of the following changes should the analyst recommend FIRST?
A. Implement File Transfer Protocol Secure on the upload server.
B. Disable anonymous login on the web server.
C. Configure firewall changes to close port 445 on 124.45.23.112.
D. Apply a firewall rule to filter the number of requests per second on port 80 on 124.45.23.108.
Correct Answer: C
Question 47
A code review reveals a web application is using time-based cookies for session management. This is a security concern because time-based cookies are easy to:
A. parameterize
B. decode
C. guess
D. decrypt
Correct Answer: C
Question 48
The threat intelligence department recently learned of an advanced persistent threat that is leveraging a new strain of malware, exploiting a system router. The company currently uses the same device mentioned in the threat report. Which of the following configuration changes would
BEST improve the organization’s security posture?
A. Implement an IPS rule that contains content for the malware variant and patch the routers to protect against the vulnerability.
B. Implement an IDS rule that contains the IP addresses from the advanced persistent threat and patch the routers to protect against the vulnerability.
C. Implement an IPS rule that contains the IP addresses from the advanced persistent threat and patch the routers to protect against the vulnerability.
D. Implement an IDS rule that contains content for the malware variant and patch the routers to protect against the vulnerability
Correct Answer: A
Question 49
A company’s change management team has asked a security analyst to review a potential change to the email server before itis released into production. The analyst reviews the following change request:
Change request date: 2020-01-30 –
Change requester. Cindy Richardson
Change asset: WIN2K-EMAILOOI –
Change requested: Modify the following SPF record to change +all to –all
Which of the following is the MOST likely reason for the change?
A. To reject email from servers that are not listed in the SPF record
B. To reject email from email addresses that are not digitally signed
C. To accept email to the company’s domain
D. To reject email from users who are not authenticated to the network
Correct Answer: A
Question 50
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:

Which of the following ports should be closed?
A. 22
B. 80
C. 443
D. 1433
Correct Answer: D
Question #51
An organization’s Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained. Which of the following roles would MOST likely include these responsibilities?
A. Data protection officer
B. Data owner
C. Backup administrator
D. Data custodian
E. Internal auditor
Correct Answer: D
Question 52
Which of the following BEST explains the function of a managerial control?
A. To scope the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To implement data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
Correct Answer: C
Question # 53
After a breach involving the exfiltration of a large amount of sensitive data, a security analyst is reviewing the following firewall logs to determine how the breach occurred.

Which of the following IP addresses does the analyst need to investigate further?
A. 192.168 1.1
B. 192.168.1.10
C. 192.168.1.12
D. 192.168 1.193
Correct Answer: C
Question 54
Employees of a large financial company are continuously being infected by strands of malware that are not detected by EDR tools. Which of the following is the BEST security control to implement to reduce corporate risk while allowing employees to exchange files at client sites?
A. MFA on the workstations
B. Additional host firewall rules
C. VDI environment
D. Hard drive encryption
E. Network access control
F. Network segmentation
Correct Answer: C
Question 55
An organization was alerted to a possible compromise after its proprietary data was found for sale on the internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output:

Which of the following should be the focus of the investigation?
A. webserver.org-dmz.org
B. sftp.org-dmz.org
C. 83hht23.org-int.org
D. ftps.bluemed.net
Correct Answer: A
Question 56
A security analyst is reviewing the network security monitoring logs listed below:

A. 10.1.1.128 sent potential malicious traffic to the web server
B. 10.1.1.128 sent malicious requests, and the alert is a false positive
C. 10.1.1.129 successfully exploited a vulnerability on the web server
D. 10.1.1.129 sent potential malicious requests to the web server
E. 10.1.1.129 sent non-malicious requests, and the alert is a false positive
F. 10.1.1.130 can potentially obtain information about the PHP version
Correct Answer: DF
Question 57
The help desk provided a security analyst with a screenshot of a user’s desktop:

For which of the following is aircrack-ng being used?
A. Wireless access point discovery
B. Rainbow attack
C. Brute-force attack
D. PCAP data collection
Correct Answer: C
Question 58
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop:

Which of the following processes will the security analyst identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
A. Chrome.exe
B. Word.exe
C. Explorer.exe
D. mstsc.exe
E. taskmgr.exe
Correct Answer: D
Question 59
An analyst is investigating an anomalous event reported by the SOC. After reviewing the system logs; the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
A. Patching logs
B. Threat feed
C. Backup logs
D. Change requests
E. Data classification matrix
Correct Answer: D
Question 60
A cybersecurity analyst is working with a SIEM tool and reviewing the following table:

When creating a rule in the company’s SIEM, which of the following would be the BEST approach for the analyst to use to assess the risk level of each vulnerability that is discovered by the vulnerability assessment tool?
A. Create a trend with the table and join the trend with the desired rule to be able to extract the risk level of each vulnerability
B. Use Boolean filters in the SIEM rule to take advantage of real-time processing and RAM to store the table dynamically, generate the results faster, and be able to display the table in a dashboard or export it as a report
C. Use a static table stored on the disk of the SIEM system to correlate its data with the data ingested by the vulnerability scanner data collector
D. Use the table as a new index or database for the SIEM to be able to use multisearch and then summarize the results as output
Correct Answer: D
Question 61
A security analyst is attempting to resolve an incident in which highly confidential company pricing information was sent to clients. It appears this information was unintentionally sent by an employee who attached it to public marketing material. Which of the following configuration changes would work BEST to limit the risk of this incident being repeated?
A. Add client addresses to the blocklist
B. Update the DLP rules and metadata
C. Sanitize the marketing material
D. Update the insider threat procedures
Correct Answer: B
Question 62
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Big Data sets Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised. Which of the following is the value of this risk?
A. $75,000
B. $300,000
C. $1,425 million
D. $1.5 million
Correct Answer: A
Question 63
A security analyst at a technology solutions firm has uncovered the same vulnerabilities on a vulnerability scan for a long period of time. The vulnerabilities are on systems that are dedicated to the firm’s largest client. Which of the following is MOST likely inhibiting the remediation efforts?
A. The parties have an MOU between them that could prevent shutting down the systems
B. There is a potential disruption of the vendor-client relationship
C. Patches for the vulnerabilities have not been fully tested by the software vendor
D. There is an SLA with the client that allows very little downtime
Correct Answer: D
Question 64
A systems administrator believes a user’s workstation has been compromised. The workstation’s performance has been lagging significantly for the past several hours. The administrator runs the task list /v command and receives the following output:

Which of the following should a security analyst recognize as an indicator of compromise?
A. dwm.exe being executed under the user context
B. The high memory usage of vscode.exe*32
C. The abnormal behavior of paint.exe
D. svchost.exe being executed as SYSTEM
Correct Answer: C
Question 65
HOTSPOT
–
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine
which process running on one of the servers may be malware.
INSTRUCTIONS
–
Servers 1, 2, and 4 are clickable. Select the Server and the process that host the malware.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 66
An organization’s Chief Information Security Officer has asked department leaders to coordinate on communication plans that can be enacted in response to different cybersecurity incident triggers.
Which of the following is a benefit of having these communication plans?
A. They can help to prevent the inadvertent release of damaging information outside the organization
B. They can help to limit the spread of worms by coordinating with help desk personnel earlier in the recovery phase.
C. They can quickly inform the public relations team to begin coordinating with the media as soon as a breach is detected
D. They can help to keep the organization’s senior leadership informed about the status of patching during the recovery phase
Correct Answer: A
Question 67
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities:

Which of the following is the MOST likely solution to the listed vulnerability?
A. Enable the browser’s XSS filter.
B. Enable Windows XSS protection.
C. Enable the private browsing mode.
D. Enable server-side XSS protection.
Correct Answer: A
Question 68
A security analyst receives a report indicating a system was compromised due to malware that was downloaded from the internet using TFTP. The analyst is instructed to block TFTP at the corporate firewall. Given the following portion of the current firewall rule set:

Which of the following rules should be added to accomplish this goal?
A. UDP ANY ANY ANY 20 Deny
B. UDP ANY ANY 69 69 Deny
C. UDP ANY ANY 67 68 Deny
D. UDP ANY ANY ANY 69 Deny
E. UDP ANY ANY ANY 69 Deny
Correct Answer: D
Question 69
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A. CIP
B. DHCP
C. SSH
D. Modbus
Correct Answer: D
Question 70
An application must pass a vulnerability assessment to move to the next gate. Consequently, any security issues that are found must be remediated prior to the next gate. Which of the following best describes the method for end-to-end vulnerability assessment?
A. Security regression testing
B. Static analysis
C. Dynamic analysis
D. Stress testing
Correct Answer: C
Question 71
As a proactive threat-hunting technique, hunters must develop situational cases based on likely attack scenarios derived from the available threat intelligence information. After forming the basis of the scenario, which of the following may the threat hunter construct to establish a framework for threat assessment?
A. Critical asset list
B. Threat vector
C. Attack profile
D. Hypothesis
Correct Answer: D
Question 72
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:

To address this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A. Reconfigure the device to support only connections leveraging TLSv1.2.
B. Obtain a new self-signed certificate and select AES as the hashing algorithm.
C. Replace the existing certificate with a certificate that uses only MDS for signing.
D. Use only signed certificates with cryptographically secure certificate sources.
Correct Answer: D
Question 73
A manufacturing company has joined the information sharing and analysis center for its sector. As a benefit, the company will receive structured IoC data contributed by other members. Which of the following best describes the utility of this data?
A. Other members will have visibility into instances of positive IoC identification within themanufacturing company’s corporate network.
B. The manufacturing company will have access to relevant malware samples from all other manufacturing sector members.
C. Other members will automatically adjust their security postures to defend the manufacturing company’s processes.
D. The manufacturing company can ingest the data and use tools to autogenerate security configurations for all of its infrastructure.
Correct Answer: B
Question 74
A security analyst scanned an internal company subnet and discovered a host with the following
Nmap output:

Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
A. Port 22
B. Port 135
C. Port 445
D. Port 3389
Correct Answer: A
Question 75
During a review of vulnerability scan results, an analyst determines the results may be flawed because a control-baseline system, which is used to evaluate a scanning tool’s effectiveness, was reported as not vulnerable. Consequently, the analyst verifies the scope of the scan included the control-baseline host, which was available on the network during the scan. The use of a control-baseline endpoint in this scenario assists the analyst in confirming:
A. verification of mitigation.
B. false positives.
C. false negatives.
D. the criticality index.
E. hardening validation.
Correct Answer: B
Question 76
A large company would like a security analyst to recommend a solution that will allow only company laptops to connect to the corporate network.
Which of the following technologies should the analyst recommend?
A. UEBA
B. DLP
C. NAC
D. EDR
Correct Answer: C
Question 77
A security operations manager wants to build out an internal threat-hunting capability. Which of the following should be the first priority when creating a threat-hunting program?
A. Establishing a hypothesis about which threats are targeting which systems
B. Profiling common threat actors and activities to create a list of IOCs
C. Ensuring logs are sent to a centralized location with search and filtering capabilities
D. Identifying critical assets that will be used to establish targets for threat-hunting activities
Correct Answer: D
Question 78
While investigating reports of issues with a web server, a security analyst attempts to log in remotely and receives the following message:

The analyst accesses the server console, and the following console messages are displayed:

The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:

Which of the following is the best step for the analyst to take next in this situation?
A. Load the network captures into a protocol analyzer to further investigate the communication with 128.50.100.23, as this may be a botnet command server.
B. After ensuring network captures from the server are saved, isolate the server from the network, take a memory snapshot, reboot, and log in to do further analysis.
C. Corporate data is being exfiltrated from the server. Reboot the server and log in to see if it contains any sensitive data.
D. Cryptomining malware is running on the server and utilizing all CPU and memory. Reboot the server and disable any cron jobs or startup scripts that start the mining software.
Correct Answer: B
Question 79
A consumer credit card database was compromised, and multiple representatives are unable to review the appropriate customer information.
Which of the following should the cybersecurity analyst do first?
A. Start the containment effort.
B. Confirm the incident.
C. Notify local law enforcement officials.
D. Inform the senior management team.
Correct Answer: B
Question 80
Security awareness and compliance programs are most effective at reducing the likelihood and impact of attacks from:
A. advanced persistent threats.
B. corporate spies.
C. hacktivists.
D. insider threats.
Correct Answer: D
